Session by Paolo Pialorsi (@PaoloPia)
In this session, you learn how authentication and authorization work in SharePoint 2013, either when handling direct users’ requests, or running requests for SharePoint apps. In particular, see how to federate with an external Identity Provider like Windows Azure ACS to authenticate users and then authorize them in SharePoint, leveraging claims.
There is one Level 400 session (highest) – guess what’s it about? Right, Authentication.
Here are my session notes.
Authentication
Classic Authentication is deprecated in SharePoint 2013. So its all about Claims now. The though thing is to map the incoming tokens from the authentication provider to the ones SharePoint use.
Identity Provider
Paolo showed an example how to utilize Facebook to log into SharePoint via Azure ACS. As said, he had to map the incoming claims token to SharePoint properties – trust the certificate on the SharePoint site and that’s it basically.
You can create a custom Identity Provider, there is a every well documented example by Steve Peschka.
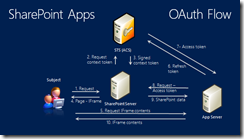
Apps
After the theory Paolo showed us how to utilize this knowledge in combination with apps. This is my favorite diagram about this:
This is crazy stuff – but very powerful.
Session Slides and Recording
The presentation and the recording will be available at the Chanel 9 site. I recommend you to watch the recording, the demos are not visible in the slides at all.
My evaluation
Authentication/Security is tough stuff: I did something similar with ADFS for a client, I wish I had this information earlier – it helped me understand what’s happening under the hood. Too bad that there are not that many advanced sessions, I wish there were more. Thanks Paolo for my better understanding about this topic!



Share this post
Twitter
Facebook
LinkedIn
Email